WiFi module
This module analyses IEEE 802.11 frames either acquired using the WiFi monitoring feature (see WiFi interface settings) or encapsulated in special packets (https://www.wireshark.org/docs/dfref/p/peekremote.html). It also provides statistics when analyzing PCAPs with a Radiotap link type and IEEE 802.11 packets.
Statistics
Channel statistics
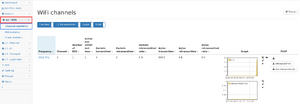
This page shows a list of all WiFi channels on which traffic is seen and offers the ability to capture the traffic of each channel. The table contains the following data:
- Frequency: the frequency of the channel in MHz. This uniquely identifies a channel as the channel numbers themselves are ambiguous.
- Channel: the channel number. These numbers are ambiguous as there exists a channel 1 in the 2.4GHz range as well as in the 5GHz range.
- Number of BSS: The number of BSS active on this channel.
- Active BSS within the last hour: the number of BSS that were active on this channel during the last hour.
- Packets: the number of packets seen on this channel.
- Packets retransmitted: the number of retransmitted[1] packets seen on this channel. (firmware >= 4.2)
- Bytes: the number of bytes seen on this channel.
- Bytes retransmitted: the number of retransmitted[1] bytes seen on this channel. (firmware >= 4.2)
- Graph: Multigraph selection that can show packet rate and data rate history.
- PCAP: Download all/only retransmitted[1]/not retransmitted[1] packets of the channel
The channel frequency can be clicked on get a list of BSS in that specific channel. This table contains the same information as the global table in the BSS statistics.
BSS statistics
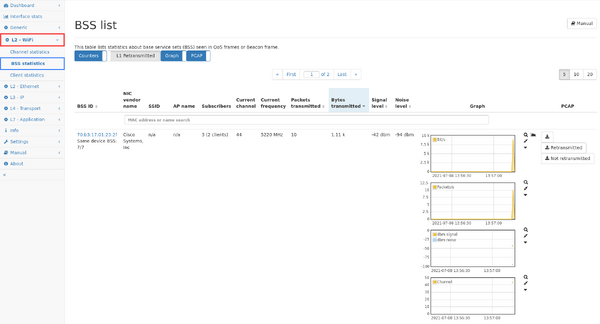
The table shown on this page lists all so-called "base service sets" which are usually the access points and offers the ability to capture the traffic of each BSS.
The table contains the following data:
- BSS ID: This is the MAC address of the station.
- In firmware >= 3.4, we also show the number of other BSS IDs of the same device, based on their MAC addresses. When following the link to the BSS detail page, the other BSS are listed on that page.
- NIC vendor name: This is the vendor name of the MAC addresse.
- SSID: When available, the SSID is shown for this BSS (firmware >= 3.4)
- AP name: When available, the AP name is shown (firmware >= 3.4)
- Note: The AP name is Cisco specific extension of beacon frame attributes and therefore only available for specific devices.
- Subscribers: This column shows the number of MAC addresses communication from or to this BSS (Firmware >= 3.4)
- The number of clients in parentheses are the number of unicast addresses different than the BSS MAC address.
- The actual subscribers can be seen in the BSS detail page.
- Current channel: This is the channel the BSS is currently operating on (firmware >= 3.4)
- Current frequency: This is the frequency the BSS is currently operating on (firmware >= 4.0)
- Current channel utilization: This value is extracted from beacon frames indicating the percentage of time the channel was active (firmware >= 3.4)
- Current frequency: This classifies the BSS frequency into 2.4 GHz, 5 GHz, or 0 for other frequencies
- packets transmitted: This is the number of packets that have been analyzed for this BSS. (firmware >= 4.2)
- packets retransmitted: This is the number of retransmitted[1] packets that have been analyzed for this BSS. (firmware >= 4.2)
- packets retransmitted ratio: This is the proportion of retransmitted[1] packets that have been analyzed for this BSS. (firmware >= 4.2)
- bytes transmitted: This is the number of bytes that have been analyzed for this BSS.
- bytes retransmitted: This is the number of retransmitted[1] bytes that have been analyzed for this BSS. (firmware >= 4.2)
- bytes retransmitted ratio: This is the proportion of retransmitted[1] bytes that have been analyzed for this BSS. (firmware >= 4.2)
- Signal/noise level: These values indicate the signal quality of the BSS.
- It uses information from packets sent from or to the BSS to give an indication ab out the overall quality.
- Graph: Multigraph selection for detailed information over time:
- Packets: this is the number of frames seen over time
- Packets retransmitted: this is the number of retransmitted[1] frames seen over time (firmware >= 4.2)
- Bytes: this is the number of bytes seen over time
- Bytes retransmitted: this is the number of retransmitted[1] bytes seen over time (firmware >= 4.2)
- dbm signal/noise: the signal and noise level over time
- Channel: This is the channel used at any given time (firmware >= 3.4)
- PCAP: Download all/only retransmitted[1]/not retransmitted[1] packets of the BSS
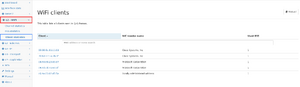
Client statistics
This page shows all clients devices (unicast devices other than BSS) that have been seen in QoS and beacon frame.
The table shows the client MAC address, its vendor name and in how many BSSs this client was active.
When clicking on the client address, a detailed page is shown. The BSS tab shows which BSS were actually used at which time so it is possible to identify how often a client switched access points.
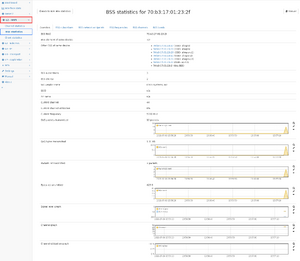
Per-BSS statistics
For each BSS MAC address, more detailed information can be shown by clicking on the MAC address in the BSS list.
The detail page shows an overview for this BSS ID and contains additional tabs for the list of subscribers and network endpoints of that base service set, as well as the list of frequencies, channels, and bands used by this base service set.
The overview tab shows all information from the BSS table and also all MAC addresses of other BSS that are handled by the same physical device.
BSS-Client details
In the BSS subscribers list on the BSS details page, information for each subscriber in the BSS is shown. A subscriber is any MAC that has sent a unicast frame to the BSS. This table contains a "Handshakes seen" column which displays the number of handshakes a client has attempted with the BSS. Clicking on the "Details" link leads to a new details page for the BSS/Client pair.
This page displays information about the client profile and the most recent handshake. The client profile contains the decoded data transmitted by the client in a (re)association request frame. It contains information about the capabilities of the client (this includes supported operating frequencies, power saving mechanisms, cryptographic ciphers, beamforming information, ...). Each category is collapsible by clicking on the title text, and some of the categories are collapsed by default.
The "Handshake" tab displays the most recently seen handshake (successful or not) as a flowchart diagram. The page consists of the diagram on the left side, and a details panel on the right side. Clicking on an element in the flowchart will populate the details panel with additional information about the frame (if available). To the left of the flowchart there are timestamps (in absolute and relative format) showing when a frame was sent.
The handshake analysis also evaluates the correctness of the handshake. If a frame does not adhere to the IEEE802.11 specification (for example the client sends an association request before authenticating with the BSS) or a frame contains invalid information these frames will be marked as invalid. Frames that are technically allowed but unexpected at the current stage of the handshake (for example spurious probe requests after association) are marked as dubious. Dubious frames are unproblematic under normal circumstances. An invalid frame might be an indicator of a misconfigured WiFi device or poor signal quality at the Allegro Multimeter's location. Incident rules can be created to trigger when invalid handshake frames are seen, or when a handshake fails (for whatever reason).
The following details are displayed in the details panel:
| Authentication algorithm | The algorithm used for authentication with the BSS. Usually "Open Systen" indicates WPA2, and "SAE" indicates WPA3 |
| Sequence number | The current step in the authentication process |
| Status | The status code of the authentication |
| Capabilities | A list of capabilities the responder has. This is an overview of the client profile of the responder |
| Status | The status code of the association |
| Association ID | An ID given to the client by the BSS, used in future reassociations. |
| Reason | A code describing the reason why the client (was) deauthenticated/disassociated |
| Descriptor version | Describes the cryptographic authentication and key management mechanism used in the handshake |
| Key type | Whether this frame is part of the 4-way handshake |
| Install | Whether the client shall install the key derived from this frame |
| Key Ack | Whether the client needs to respond to this frame |
| Key MIC | Whether or not this frame contains a MIC |
| Secure | Set to "true" once initial key exchange is complete (EAPOL-Key 3 and onwards) |
| Error | Whether an error occured during the handshake |
| Request | Set to "true" by the client when they request the initiation of a handshake |
| Encrypted Key Data | Whether the key data in this frame is encrypted |
| Key length | Length of the temporal key |
| Key replay counter | Number of exchanges carried out during this handshake |
| Key nonce, IV, RSC, MIC | Cryptographic values used in the key derivation |
| Key data length | Length of the key data (0 means no key data is present) |
| Key Data | Key Data |
Traffic processing
There are currently four kinds of 802.11 traffic that can be analyzed:
- Live packet processing of IEEE 802.11 packets acquired with the WiFi monitoring feature (see WiFi interface settings).
- Radiotap PCAP files that contain IEEE 802.11 packets.
- PEEKREMOTE packets. This kind of traffic is generated by access points and is send via UDP to a specified IP address and port. To analyze this traffic, the endpoint mode has to be enabled on an interface which receives this traffic. In the endpoint mode configuration, an IP address and port can be configured for which the Allegro Network Multimeter accepts packets. PEEKREMOTE packets usually do not contain complete IP packets, only 802.11 statistics that are evaluated by the Allegro Network Multimeter.
- CAPWAP encapsulated packets. In contrast to PEEKREMOTE, CAPWAP packets encapsulate complete IP packets which itself contain 802.11 information. Therefore, the endpoint mode must be configured for a specific IP and port and the tunnel view mode must be enabled too to let the Allegro Network Multimeter look inside the encapsulated packets.